IDENTIFYING RED FLAGS AND SYMPTOMS OF FRAUD
Introduction
When we refer to red flags, it means the various situations or conditions that, over the years, have consistently been shown to be contributing factors to fraud, waste and abuse. By themselves, they don’t necessarily mean anything, but the more that are present, the higher the risk that fraud, waste and abuse is occurring, or could occur.
There are two general categories of offenders – internal and external. Many government programs have external customers, such as contractors, grantees, or others who potentially can misrepresent facts to obtain money they are not entitled to. Internal offenders are people who use their positions within an organization for personal enrichment through the deliberate misuse or misapplication of the organization’s resources or assets. The red flags identified here ought to aid in identifying fraud in both categories of offenders.
Red Flags
Opportunity Red Flags
Fraud Conducted By Employees against the Organization
• Familiarity with operations (including cover-up capabilities and in a position of trust)
• Close association with suppliers and other key people
• Rapid turnover of key employees either by quitting or firing
• No mandatory vacations, periodic rotations, or transfers of key employees
• Inadequate personnel-screening policies when hiring new employees to fill positions of trust
• Operating on a crisis basis
• Unrealistic productivity measurements
• Poor compensation practices
Fraud Conducted By Individuals On Behalf Of The Organization
• Related party transactions – less than arm’s length bargaining
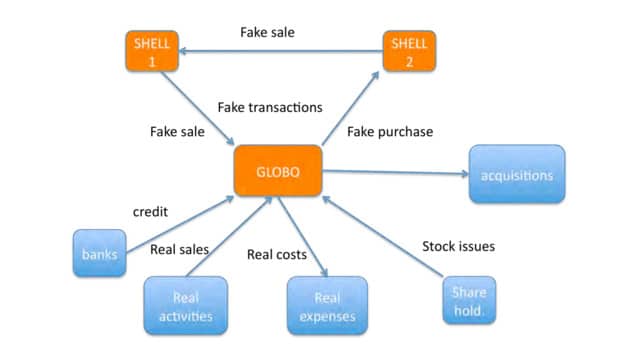
• A complex business structure – often unnecessarily complex business structures are created to hide fraudulent activity and money laundering.
• No effective internal auditing function
• An organization that uses several different auditing firms or changes auditors often
• An organization that is reluctant to give auditors needed data
• An organization that uses several different legal firms or changes legal counsel often
• An organization that uses an unusually large number of different banks, none of which can see the entire picture
• Continuous problems with various regulatory agencies
• Large year-end and/or unusual transactions or adjusting entries to accounting records
• An inadequate internal control system or no enforcement of the existing internal controls
• Unduly liberal accounting practices
• Poor accounting records and inadequate staffing in the accounting department
• An organization that inadequately discloses questionable or unusual accounting practices
Some circumstances that might contribute to fraud include:
• Weak internal control environment
• Management does not emphasize the role of strong internal controls
• Management does not prosecute or punish identified embezzlers
• Management does not have a clear position about conflicts of interest
• Highly placed executives are less than prudent or restrained on expenditures for travel and entertainment, furnishings of offices, gifts to visitors and directors, etc.
• Internal auditing does not have authority to investigate certain executive activities involving heavy personal expenditures
• Accounting policies and procedures are on the lax or loose side
SITUATIONAL PRESSURE RED FLAGS
Fraud Committed By Employees Against The Organization
• Significant observed changes from past behavior patterns
• High personal debts or financial losses
• Inadequate income for lifestyle
• Extensive stock market or other speculation behavior
• Excessive gambling
• Undue family, organization, or community expectations
• Excessive use of alcohol or drugs
• Perceived inequities in the organization
• Resentment of superiors and frustration with job
• Peer group pressures
• Undue desire for self-enrichment and personal gain
• Emotional trauma in home life or work life
Fraud Committed By Management On Behalf Of The Organization
• Unfavorable economic conditions within the industry
• Pressure tactics by contractors or grantees to allow questionable costs
• Dependence on one or two products, customers, or transactions
• Obsolescence – the product, the service – the need for an organization no longer existing.
• High debt
• Substantial growth beyond the industry norm. Rapid expansion through new business or product lines often leads to control issues and chaotic management.
• Reduced ability to acquire credit or restrictive loan agreements
• Financial difficulties such as frequent cash flow shortages, declining sales and/or profits, loss of market share, costs and expenses rising higher and faster than sales and revenues
• Difficulty in collecting receivables – high bad debt expenses and aged receivables 90 days or greater, depending on industry.
• Significant tax adjustments
• Urgent need for favorable earnings to support high price of stock or to meet earnings forecast – trying to meet investor expectations
• Need to gloss over a temporarily bad situation in order to maintain management position and prestige
• Significant litigation, especially between stockholders and management o Unmarketable collateral o Significant reduction in sales backlogs (indicates future sales have declined) Possibility of license being revoked or imperiled, especially if it is necessary for the continuation of business
• Pressure to merge
• Sizable inventory increase without comparable sales increases
• Consistently late reports
• Managers who regularly assume subordinates duties
• Noncompliance with corporate directives and procedures
• Payments to trade creditors supported by copies instead of originals
• Commissions not in line with increased sales Unable to verify the existence of vendors, subcontractors
Personal Characteristic Red Flags
Warning Signals Should Go Off When Employees Evidence Characteristics Such As:
• Rationalization of contradictory behavior
• Lack of a strong code of personal ethics
• A strong desire to beat the system
• A criminal or questionable background
• A poor credit rating and financial status
• Highly materialistic and self-centered
• Are often eccentric in the way they display their wealth or spend their money
• Are reckless or careless with facts and often twist facts to fit their agenda
• Often they may appear to be hard working, almost compulsive, but most of their time at work is spent scheming and designing short cuts to get ahead or beat the competition.
• May demonstrate hostility toward people who oppose their views
• Feel exempt from accountability and controls because of their station or position
• Tendency to override internal controls with impunity and argue forcefully for less formality in controls
With internal offenders, research has shown that about 2/3 of crime is attributable to employees, while 1/3 is attributable to managers and executives. However, the median loss in employee cases was about 14 times less than when a manager/executive was involved. Frauds typically involve a trust element to make them work, and with internal offenders, the research bore out that the longer an employee has been with an organization, the higher the loss tended to be. This is attributed to the fact that most employees gain more responsibility and trust the longer they are with an organization.
Indicators Of Possible Fraudulent Activities
Transactions that are different or unusual (without explanation) or suspicious as to:
• Time (of day, week, month, year, or season)
• Frequency (too many, too few)
• Places (too far, too near, and too “Far out”)
• Amount (too high, too low, too consistent, too alike, too different)
• Parties or personalities (related parties, oddball personalities, strange and estranged relationships between parties, i.e., management performing clerical functions).
Discrepancies in Accounting Records
• Account balances that are significantly over or understated
• Transactions not recorded in a complete or timely manner or improperly recorded as to amount, accounting period, classification, or organization policy
• Unsupported or unauthorized records, balances, or transactions
• Last minute client adjustments that significantly affect financial results (particularly those increasing income presented after submission of the proposed audit adjustments)
• Excessive number of adjusting entries, and repetitive use of adjusting entries for no apparent purpose.
Conflicting or Missing Evidential Matter
• Suspicious or missing documents
• Unexplained items on reconciliations
• No original documents available – only photocopied documents
• Inconsistent, vague or implausible responses arising from inquiries or analytical procedures
• Unusual discrepancies between the client’s records and confirmation replies
• Missing inventory or physical assets
• Excessive voids or credits
• Shifting of costs from one category or cost account to another
• Common names or addresses of payees or customers – inability to verify the existence of vendors/subcontractors
• Alterations on documents (e.g. back dating, white-out)
• Duplications (e.g., duplicate payments)
• Questionable handwriting on documents
Unusual Relationships
• Appearance of a conflict of interest
• Less than arms length bargaining
• Related party transactions
• Denied access to records or facilities
• Denied access to certain employees, customers, vendors, or others from whom program managers may seek to obtain information from
• Undue time pressures imposed by management to resolve complex or contentious issues
• Unusual delays in providing requested information
• Tips or complaints about fraud, including whistleblowers inside the organization.
Other Concerns
• Significant internal control weaknesses or prior year internal control weaknesses not corrected
• Unexplained increases in costs or claims
• Suspicious, unexpected or unusual trends or shifts in activity.
• Unusual transactions (e.g., for activities outside the normal line of business)
• Changes in accounting principles or the methods of applying them that enhances reported income
• Departure of key financial or operating personnel
• Specific instances of management’s conduct that raise serious concerns as to their integrity
Characteristics Of Top-Management Fraud
Top Management Defrauders
a) Tend to have highly material personal values.
b) Success to them means financial success, not professional recognition.
c) Tend to treat people as objects, not individuals and often as objects for exploitation.
d) Are highly self-centered.
e) Are often eccentric in the way they display their wealth or spend their money.
f) They tend to be conspicuous consumers and often boast of the things they have acquired, the friends they have in high office, and all the fine places they have visited.
g) Speak about their cunning achievements and winnings more than their losses.
h) Appear to be reckless or careless with facts and often enlarge on them.
i) Appear to be hard working, almost compulsive, but most of their time at work is spent scheming and designing short cuts to get ahead or beat the competition.
j) May gamble or drink a great deal.
k) Buy expensive gifts for their families usually to compensate for spending so little time with them.
l) Are hostile to people who oppose their views.
m) They feel exempt from accountability and controls because of their station or position.
n) Create a great deal of turnover among their subordinates and often set off one subordinate against the other.
o) Play favorites among subordinates, but the relationship can cool very quickly because a subordinate often falls from grace after one mistake, even an insignificant one.
p) Manage by crisis more often than by objectives.
q) Tend to drift with the times and have no long-range plans, tend to override internal controls with impunity and argue forcefully for less formality in controls.
r) Demand absolute loyalty from subordinates, but they themselves are loyal only to their own self-interests.
s) Have few real friends within their own industry or company.
t) Their competitors and colleagues often dislike them.
Interpreting Potential Red Flags
It is not, of course, as easy as it sounds to identify and interpret potential red flags. First, flags is a bit of a misnomer and creates a false impression of plainly visible warning signs. While this is true of some frauds, it is important to remember that fraud is fundamentally a crime of deception and deceit. Calling to mind a mental picture of a scarcely visible red thread waving in the wind is more accurate than picturing a bold red flag. Some of the difficulties inherent in identifying and interpreting potential red flags are summarized in the following:
i. Fraud risk factors are not the same as evidence of fraud. Risk factors are not evidence of fraud. To the extent that risk factors are evidence of anything, they point to an environment or situation in which there is an increased risk that material misstatement due to fraud might occur either generally or in a specific functional or geographic sector of the entity’s operations.
Individuals may be motivated by the prospect of bonuses and other incentives to manipulate results to their advantage and in a manner that may amount to fraud. Several high-profile instances of financial statement fraud have been motivated in part by bonus and incentive arrangements. As an example, a chairman and CEO was accused of earning substantial bonuses and profiting on the sale of shares in the company on the basis of fraudulent financial reporting that misrepresented the company’s results. This does not mean, of course, that the presence of bonus and other incentive schemes is prima facie evidence of fraudulent financial reporting, but it may be considered in the overall risk assessment.
Another example of a fraud risk factor is the so-called dominant CEO. Even absent a dominant CEO, similar risks can emerge whenever corporate governance is weak—for example, when power is concentrated in the hands of senior management without an effective counterbalance from the board. No one would seriously suggest, however, that the existence of a CEO with a forceful personality and a strong sense of mission is indicative of fraud. It is simply a risk factor.
ii. Fraud risk factors may indicate the existence of risks other than fraud. Many risk factors are not exclusively indicative of fraud risk. They may also suggest a heightened risk of material misstatements due to human or process error. For example, deficiencies in internal controls may be regarded as fraud risk factors, but they also pose the risk that errors may occur and go undetected without any intent to commit fraud. Sometimes, weak internal controls simply fail to limit or identify accounting or reporting mistakes. The auditor should not discount either possibility without reasonable grounds for doing so.
iii. Fraud risk factors can be ambiguous. Many fraud risk factors are susceptible to both innocent and sinister interpretations. The fact that a company has a complex structure with a large number of overseas subsidiaries and significant intra company trading may indicate an increased fraud risk, or it may simply be a legitimate characteristic of that business. On one hand, that a ledger clerk drives a car he appears to be unable to afford may indicate a risk that he has misappropriated company assets. On the other hand, he and his wife may have a two-income household that allows them certain luxuries. The focus must be on fact-finding and critical assessment of cumulative evidence.
iv. There is no linear relationship between the number of fraud risk factors and the level of fraud risk. It may be that, in general, the more risk factors the auditor identifies in a client, the greater the overall risk of fraud. But even a few risk factors in key areas may be grounds for concern. A simplistic attempt to quantify fraud risk by a count of risk factors is misguided. The objective is not to estimate how likely it is that a material misstatement due to fraud will occur but, rather, to identify where and in what manner that might happen.
v. Fraud risk factors are of limited significance in isolation. In general, individual risk factors are of limited significance in isolation. Rather, they need to be considered as a whole. The point about the dominant CEO factor, for example, is that it may actually contain a number of separate risk factors that when looked at together, create a risk situation: a bullying CEO, lack of counterweight among other senior executives, and apparent absence of an effective audit committee, supervisory board, or similar corporate governance function. The auditor attempts to interpret evidence of potential risk factors within the wider context of other observations about the company, its management, and the business environment in which it operates. Nonetheless, the identification of an anomaly or loose thread can lead to the identification of multiple risk factors and control weaknesses or actual instances of financial statement fraud or misappropriation of assets. The auditor considers whether one particular risk factor may, in fact, be linked to one or more other factors.
vi. Some fraud risk factors are very difficult to observe. Certain fraud risk factors are essentially states of mind or related to an individual’s private life or personal financial affairs. They may be impossible to observe directly. The auditor might nonetheless become aware of indirect signs that relevant states of mind or privatelife factors may exist. All of these issues increase the challenge faced by the auditor in trying to identify indications of the existence of fraud risk within the substantial body of information available from the audit process. SAS 99 distinguishes between risk factors relevant to the risk of material misstatement due to fraudulent financial reporting and those relevant to the risk of material misstatement arising out of the misappropriation of assets. In practice, as the standard acknowledges, many risk factors are potentially common to both kinds of misstatement. Risk factors related to weaknesses in control or supervision may, for example, be equally applicable to either type of fraud.
Symptoms of Fraud
A person’s lifestyle may change, a document may be missing, a general ledger may be out of balance, someone may act suspiciously, a change in an analytical relationship may not make sense, or someone may provide a tip that fraud is occurring. Unlike videos in robbery or bodies in a murder, however, these factors are only symptoms rather than conclusive proof of fraud. There may be other explanations for the existence of these symptoms. Lifestyle changes may have occurred because of inherited money. Documents may have been legitimately lost. The general ledger may be out of balance because of an unintentional accounting error. Suspicious actions may be caused by family dissension or personal problems. Unexplained analytical relationships may be the result of unrecognized changes in underlying economic factors. A tip may be motivated by an envious or disgruntled employee’s grudge or by someone outside the company desiring to settle a score.
To detect fraud, managers, auditors, employees, and examiners must recognize these fraud indicators or symptoms (sometimes called red flags) and investigate whether the symptoms resulted from actual fraud or were caused by other factors. Unfortunately, many fraud symptoms go unnoticed, and even symptoms that are recognized are often not vigorously pursued. Many frauds could be detected earlier if fraud symptoms were investigated.
Symptoms of fraud can be separated into six groups: (1) accounting anomalies, (2) internal control weaknesses, (3) analytical anomalies, (4) extravagant lifestyle, (5) unusual behavior, and (6) tips and complaints. In this section, we briefly discuss these six types of symptoms.
1. ACCOUNTING ANOMALIES
Common accounting anomaly fraud symptoms involve problems with source documents, faulty journal entries, and inaccuracies in ledgers. We discuss each of them in the following section.
Irregularities in Source Documents
Common fraud symptoms involving source documents (either electronic or paper)—such as cheques, sales invoices, purchase orders, purchase requisitions, and receiving reports—include the following:
• Missing documents
• Stale items on bank reconciliations
• Excessive voids or credits
• Common names or addresses of payees or customers
• Increased past-due accounts
• Increased reconciling items
• Alterations on documents
• Duplicate payments
• Second endorsements on checks
• Document sequences that do not make sense
• Questionable handwriting on documents
• Photocopied documents
Faulty Journal Entries
Accounting is a language, just as English and Japanese are languages. For example, consider the following journal entry:
Legal Expense …………………………………….5,000
Cash …………………………………….5,000
In the English language, this entry says, “An attorney was paid $5,000 in cash.” In the language of accounting, this entry says, “Debit Legal Expense; credit Cash.” A person who speaks both accounting and English will realize that these statements say exactly the same thing.
The problem with the language of accounting is that it can be manipulated to tell a lie, just as can English or Japanese or any other language. For example, with the above entry, how do you know that an attorney was actually paid $5,000? Instead, maybe an employee embezzled $5,000 in cash and attempted to conceal the fraud by labeling the theft as a legal expense. Smart embezzlers sometimes conceal their actions in exactly this way, realizing that the fraudulent legal expense will be closed to Retained Earnings at the end of the accounting period, making the audit trail difficult to follow. And, if the fraudulent employer routinely pays large amounts of legal expenses, this small fraud could easily go unnoticed. To understand whether journal entries represent truth or are fictitious, one must learn to recognize journal entry fraud symptoms.
An embezzler usually steals assets, such as cash or inventory. (No one steals liabilities!) To conceal the theft, the embezzler must find a way to decrease either the liabilities or the equities of the victim organization. Otherwise, the accounting records will not balance, and the embezzler will be quickly detected. Smart embezzlers understand that decreasing liabilities is not a good concealment method. In reducing payables, amounts owed are eliminated from the books. This manipulation of the accounting records will be recognized when vendors do not receive payments for amounts owed to them. When the liability becomes delinquent, they will notify the company. Subsequent investigation will usually reveal the fraud.
Smart embezzlers also realize that most equity accounts should not be altered. The owners’ equity balance is decreased by the payment of dividends and expenses and is increased by sales of stock and by revenues. Embezzlers rarely conceal their frauds by manipulating either dividends or stock accounts because these accounts have relatively few transactions and alterations can be quickly noticed. In addition, transactions involving stocks or dividends usually require board of director approval, go through a transfer agent, and are monitored closely.
Thus, income statement accounts such as revenues and expenses remain as possible accounts for decreasing the right side of the accounting equation and making the accounting records balance when stealing an asset. Balancing the equation by manipulating revenues would require that individual revenue accounts be reduced. However, since revenues rarely decrease (except through adjusting entries at the end of an accounting period), a decrease in a revenue account would draw attention. Therefore, embezzlers who manipulate accounting records to conceal their frauds usually attempt to balance the accounting equation by increasing expenses. Increasing expenses decreases net income, which decreases retained earnings and owners’ equity, thus leaving the accounting equation in balance, as illustrated in Figure below.
Recording an expense to conceal fraud involves making a fictitious journal entry. Fraud examiners must be able to recognize signals that a journal entry may have been manufactured to conceal a fraud. Manipulating expense accounts also has the advantage that expenses are closed or brought to zero balances at year-end, thus obscuring the audit trail. The following are common journal entry fraud symptoms:
• Journal entries without documentary support
• Unexplained adjustments to receivables, payables, revenues, or expenses
• Journal entries that do not balance
• Journal entries made by individuals who would not normally make such entries
• Journal entries made near the end of an accounting period.
Inaccuracies in Ledgers
The definition of a ledger is “a book of accounts.” In other words, all transactions related to specific accounts, such as cash or inventory, are summarized in the ledger. The accuracy of account balances in the ledger is often proved by ensuring that the total of all asset accounts equals the total of all liability and equity accounts or, if revenues and expenses have not yet been closed out, that the total of all debit balances equals the total of all credit balances. Many frauds involve manipulating receivables from customers or payables to vendors. Most companies have master (control) receivable and payable accounts, the total of which should equal the sum of all the individual customer and vendor account balances. Two common fraud symptoms relating to ledgers are as follows:
1. A ledger that does not balance; that is, the total of all debit balances does not equal the total of all credit balances.
2. Master (control) account balances that do not equal the sum of the individual customer or vendor balances.
The first symptom is indicative of a fraud in which cover-up in the accounting records is incomplete. For example, a perpetrator may embezzle inventory (an asset) but not reflect the reduction of inventory in the accounting records. In this case, the actual inventory balance, as determined by a physical count, is lower than the recorded amount of inventory, and the ledger does not balance. Another example of a ledger out of balance is the theft of cash accompanied by the failure to record an expense. In this case, total assets would be less than total liabilities plus owners’ equity.
The second ledger symptom is indicative of manipulation of an individual customer’s or vendor’s balance without altering the master receivable or payable account in the ledger.
In this case, the sum of the individual customer or vendor balances does not agree with the master account balance.
2. Internal Control Weaknesses
Fraud occurs when perceived pressure, perceived opportunity, and rationalization combine. Many individuals and organizations have pressures. Everyone rationalizes. When internal controls are absent or overridden, the risk of fraud is great. Internal control is comprised of the control environment, the accounting system, and control procedures.
Common internal control fraud symptoms include the following:
• Lack of segregation of duties
• Lack of physical safeguards
• Lack of independent checks
• Lack of proper authorization
• Lack of proper documents and records
• Overriding of existing controls
• Inadequate accounting system
3. Analytical Fraud Symptoms
Analytical fraud symptoms are procedures or relationships that are unusual or too unrealistic to be believable. They include transactions or events that happen at odd times or places; that are performed by or involve people who would not normally participate; or that include odd procedures, policies, or practices. They also include transactions and amounts that are too large or too small, that are performed or occur too often or too rarely, that are too high or too low, or that result in too much or too little of something. Basically, analytical symptoms represent anything out of the ordinary.
They are the unexpected. Common examples of analytical symptoms include the following:
• Unexplained inventory shortages or adjustments
• Deviations from specifications
• Increased scrap
• Excess purchases
• Too many debit or credit memos
• Significant increases or decreases in account balances, ratios, or relationships
• Physical abnormalities
• Cash shortages or overages
• Excessive late charges
• Unreasonable expenses or reimbursements
• Excessive turnover of executives
• Strange financial statement relationships, such as:
_ Increased revenues with decreased inventory
_ Increased revenues with decreased receivables
_ Increased revenues with decreased cash flows
_ Increased inventory with decreased payables
_ Increased volume with increased cost per unit
_ Increased volume with decreased scrap
_ Increased inventory with decreased warehousing costs
4. Extravagant Lifestyles
Most people who commit fraud are under financial pressure. Sometimes the pressures are real; sometimes they merely represent greed. Once perpetrators meet their financial needs, they usually continue to steal, using the embezzled funds to improve their lifestyles.
Often, they buy new cars. They sometimes buy other expensive toys, take vacations, remodel their homes or move into more expensive houses, buy expensive jewelry or clothes, or just start spending more money on food and other day-to-day living expenses. Very few perpetrators save what they steal. Indeed, most immediately spend everything they steal. As they become more and more confident in their fraud schemes, they steal and spend larger amounts. Soon they are living lifestyles far beyond what they can afford. To illustrate how people’s lifestyles change when they embezzle, consider the following two examples.
John Kate embezzled nearly $3 million from her employer. She and her husband worked together to perfect the scheme over a period of seven years. Because they knew they might someday get caught, they explicitly decided not to have children. With their stolen funds, they purchased a new, expensive home (supposedly worth $500,000) and five luxury cars—a Maserati, a Rolls-Royce, a Jeep Cherokee, and two Audis. They filled their home with expensive artwork and glass collections. They bought a boat and several expensive computers, and they paid cash to have their yard extensively landscaped. They frequently invited Kate’s coworkers to parties at their home and served expensive foods, including lobster flown in from the east coast. Yet none of the employees noticed the change in lifestyle. They did not note, for example, that Kate drove a different car to work every day of the week and that all her cars were extremely expensive.
In the second case, Randy stole over $600,000 from his friend’s small company, for which he worked. The business constantly had cash flow problems, but Randy drove a Porsche, bought a cabin in the mountains, and took expensive vacations. At one point, he even loaned his friend $16,000 to keep the business going. Never once did the owner question where the money was coming from, even though Randy was being paid less than $25,000 per year.
Embezzlers are people who take shortcuts to appear successful. Very few crooks, at least those who are caught, save embezzled money. The same motivation for stealing seems to also compel them to seek immediate gratification. People who can delay gratification and spending are much less likely to possess the motivation to be dishonest.
Lifestyle changes are often the easiest of all symptoms to detect. They are often very helpful in detecting fraud against organizations by employees and others but not as helpful in detecting fraud on behalf of a corporation, such as management fraud. If managers, coworkers, and others pay attention, they notice embezzlers living lifestyles that their incomes do not support. While lifestyle symptoms provide only circumstantial evidence of fraud, such evidence is easy to corroborate.
5. Unusual Behaviors
Research in psychology reveals that when a person (especially a first-time fraud perpetrator) commits a crime, he or she becomes engulfed by emotions of fear and guilt.
These emotions express themselves as stress. The individual often exhibits unusual and recognizable behavior patterns to cope with the stress, as shown in Figure below. No particular behavior signals fraud; rather, changes in behavior are signals. People who are normally nice may become intimidating and belligerent. People who are normally belligerent may suddenly become nice.
Even perpetrators recognize their behavioral changes. A woman who stole over $400,000 said, “I had to be giving off signals. I could not look anyone in the eye.” A man who embezzled over $150,000 said, “Sometimes I would be so wound up I would work 12 or 14 hours a day, often standing up. Other times I would be so despondent I could not get off the couch for over a week at a time.”
6. Tips and Complaints
Auditors are often criticized for not detecting more frauds. Yet, because of the nature of fraud, auditors are often in the worst position to detect its occurrence. As we covered previously, the factors that lead to fraud are depicted in the fraud triangle. These factors consist of pressure, opportunity, and rationalization. As you may recall, the elements of fraud can be illustrated as shown in Figure below.
The theft act involves the actual taking of cash, inventory, information, or other assets. Theft can occur manually, by computer, or by telephone. Concealment involves the steps taken by the perpetrator to hide the fraud from others. Concealment can involve altering financial records, miscounting cash or inventory, or destroying evidence. Conversion involves selling stolen assets or transferring them into cash and then spending the cash. If the asset taken is cash, conversion means merely spending the stolen funds. As we have noted previously, virtually all perpetrators spend their stolen funds.
Fraud can be detected in all three elements. First, in the theft act, someone can witness the perpetrator taking cash or other assets. Second, in concealment, altered records or miscounts of cash or inventory can be recognized. Third, in conversion, the lifestyle changes that perpetrators almost inevitably make when they convert their embezzled funds are visible.